Archived from the original on 16 February Source code can be changed, Hoglund conceded, but economics make it unlikely it will be changed often. Open Source Fingerprint Tool From: I agree to this site's Privacy Policy. Technical users can also use Tails to help ensure you do not leave any records of your submission on the computer. 
| Uploader: | Tasar |
| Date Added: | 5 March 2006 |
| File Size: | 33.47 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 83508 |
| Price: | Free* [*Free Regsitration Required] |
Marks created during software development can provide tracks. Retrieved 3 June If you do this and are a high-risk source you should make sure there are no traces of the clean-up, since such traces themselves may draw suspicion. Archived from the original on 16 February WikiLeaks publishes documents of political or historical importance that are censored or otherwise suppressed.
HBGary - Wikipedia
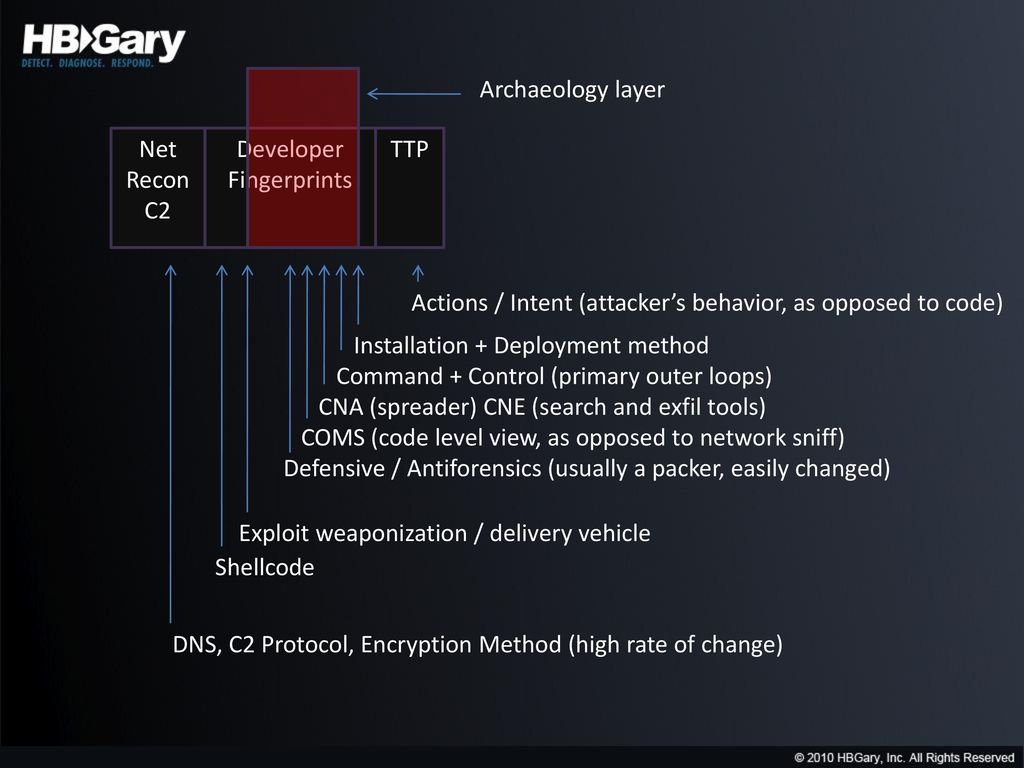
My rules just look for the existence of strings, so I identify the existence of "send" in the string "caught finyerprint sending " for example, instead of ensuring that "send" has non-ascii on either side of it, so this will have more false positives than FingerPrint. Gather all the data Step 2: Identifying the individual or the group that created the code is more complex and will require a combination of human intelligence as well hbgady technology.
The following is the address of our secure site where you can anonymously upload your documents to WikiLeaks editors. We released Fingerprint as a free download, including the source-code, so organizations can tailor it to their unique mission hbgarh help advance the technology.
Some products are integrated into other products i. William Jackson is a Maryland-based freelance writer. This could extend the useful life of a signature from days to years. Open Source Fingerprint Tool From: Inside the convoluted plot to bring down WikiLeaks".
Some of the documents taken by Anonymous show HBGary Federal was working on behalf of Bank of America to respond to WikiLeaks' planned release fingerpeint the bank's internal documents.
Chamber of Commerce contracted the firms to spy on and discredit unions and liberal groups. Archived from the original on 17 February RAM snapshots aka memory images of Windows computers [43] [44]. He has been able to determine the time at which a piece of malware used in the theft of data from a defense contractor was compiled.
GCN Newsletter
The integration is starting now. If you face legal action If a legal action is brought against you as a result of your submission, there are organisations that may help you. Companies based in Sacramento, California Computer security companies Security consulting firms. Computer software Computer security. HBGary had made numerous threats of cyber-attacks against WikiLeaks.
If you can use Tor, but need to contact WikiLeaks for other reasons use our secured webchat available at http: He identified the code as coming from a Chinese source because of the language it was written in.
Identifying malware from a common source is fkngerprint comparatively simple matter of comparing the digital fingerprints and finding a match. FingerPrint has some XML and pretty command-line output, whereas mine is more geared towards being fed into a second stage analysis fingerprijt.
If a legal action is brought against you as a result of your submission, there are organisations that may help you.
Tor is an encrypted anonymising network that makes it harder to intercept internet communications, or see where communications are fingerorint from or going to. So for example, you would want to take the output from FingerPrint and then use it to compare various binaries in order to perform clustering or associate similarity scores, but there is no discussion on how to do that maybe I'll take a swing at this in another article. Spies and researchers still will have to locate, monitor and possibly infiltrate — either in person or online — the groups producing and using the malware.
You can only access this submissions system through Tor. The targets of the code were in the Defense Department, but Hoglund said he doubted the creators were working directly for the Chinese government.

Related Articles Combat the insider threat with next-gen privileged access management Stop chasing ghosts and build a threat hunting strategy How cybercrime feeds on modernization Phishing: HBGary, considering they are only 38 peoplehas made some cool tools.

No comments:
Post a Comment